legal
We stick to the letter of the law!
As we are an online business with a global footprint and a virtually hosted organisation with specialized product-sets, specialized certified technical skills and a very strong focus on cloud technologies and systems, we pride ourselves on having a workforce that is driven by earning potential and incentive, workload, personal ability and remunerated on an agreed scale for completed tasks and achieved targets, by monitoring active hours through machine learning and compute hours, active artificial intelligence, security and cognitive recognition systems, as is afforded to anyone with appropriate knowledge and use of such systems. We employ highly skilled specialists that create, build, generate and interpret the data that these systems affords us due to modern technological advancements. We do not write in red pen and carry calculators around, we do our business electronically on highly advanced systems.
Don't worry, for the technologically impaired individuals reading this, all it means is that our data and all critical systems are hosted outside the borders of our beautiful, but unfortunately crime-ridden country and is therefore governed by and strictly under whichever country is currently hosting the clustered data, and where the system may have failed over to, which includes Northern and Western European countries, Australia and also Eastern, Western and Central States of the USA. Wherever the active node resides of the fail-over clustered set, is the jurisdiction and related regulatory information, communication and technology related laws that apply to anything information on that system.
These regions where our data-centers are located, ensure that we strictly adhere to their legislation should any information fall under their jurisdiction, at the time of any logged and time-stamped event that coincides with the recorded log of where the active fail-over node was hosted at the time the aforementioned event, and our data, security and storing compliance is in line with all relevant countries and their applicable privacy laws. Should any data-set recorded in Europe for instance, report an event and logged by agents monitoring the systems, that the data-set was active in the Central US at that specific time, due to possible GEO-redundant fail-over, the State in which the data resided in America would then have jurisdiction over same and their governing laws need to be adhered to, regardless if the data-set was retrieved from the node whilst it was active in Europe when gathering forensic information and/or data.
We know if you sell shower-heads and bathroom tiles for a living, this concept will be impossible to grasp, so we will try and make this as simple as possible by explaining rudimentary and basic network communications. The best way to say it, is that our electronic data is not governed by South African Legislation at any time, except for electronic transactions and/or records that have traversed internationally, via the internet or possibly via electronic mail or local GSM and Telecommunication infrastructure.
These systems and/or infrastructure then also have to reside and function on at least Layer 1,2, AND 3 of the Open System Interconnect Model, on South African soil, to be legally intercepted by the South African government and the recipient's system has to comply with all 7 layers to be lawfully considered a data-set accepted under South African jurisdiction (Of which The Regulation of Interception of Communications Act and The Electronic Communication and Transactions Act is most notable, should you want to reference local legislation)
Wait, maybe we should use pictures to explain this. Our venture capitalists have recently received email from a complainant that could not spell or write in English, so maybe pictures are necessary.
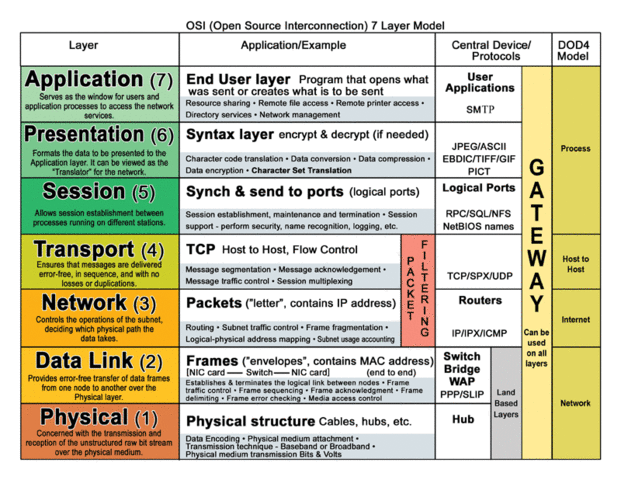
If you look at the picture above, which represents the receiving end-point's session and flow, then it will be considered unlawful under SA Legislation if the communication is intercepted and the system from which data is obtained is not physically in the RSA with relation to Level 1 through 3, then the data is unlawfully obtained and cannot be used to incriminate any juristic person under South African law, of involvement with whatever data was intercepted, by altering, creating, transmitting or destroying such data, without concrete evidence and factual data linking the suspect to the transmission of whatever cyber crime was committed.
Just be careful before you blame us because you were impersonated and we did an affordability check on you, because we don't know what you look like and who you are in the world. If you give us an ID number when we request it from you or whoever is pretending to be you, we are legally allowed, and actually obliged, to ensure you can afford the monthly costs of the services we offer before we close a sale. We will be held responsible for over-indebting you if we recklessly just hand out accounts and services to every Tom, Dick and Harry that requests information and provides us an ID Number and verbal consent to do an affordability assessment, then not doing so, granting you a service and you defaulting on payment because you're actually piss-poor, was impersonated and it wasn't you that requested the service in the first place. We honestly hope this makes sense to South African consumers. If you want more information, visit the Regulator's site at www.ncr.org.za - if you have any questions, you may ask our legal team to clear matters up, but we charge by the hour or part thereof. If you are a South African by birth, before 1994 and the transformation of our country, and you do not know the differences between the Usury Act and the NCA, or what to do in the event of suspected identity theft, confirmed theft, and processes to follow, what to lodge and who to speak to, we will gladly arrange an appointment to visit you at a place of your choosing, then demonstrate the process flow, and give you contact names and numbers of fraud prevention services and even laboratories that do forensic investigations, and we will gladly provide them with whatever data they require to prove our non-involvement in your complaint.
Again, we will gladly send you a quotation for the consultation and to provide the data you require, but we do not make house-calls if you're an uninformed individual that blames us for stealing your identity. In that instance you will be liable for any fees we may incur in proving otherwise.
Otherwise, it's business as usual and your account manager, support engineer and marketing team are all still safe and unharmed, which means your business can go on, uninterrupted. We do not have an inbound sales call-center, as our sales team seek young bright minds through technology and BI data-sets.


